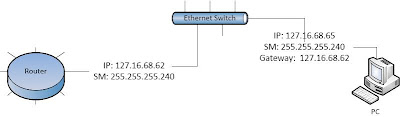
Dynamic refers to automatic update of routing table. The routing protocol defines the set of rules used by a router when it communicates routing information between neighboring routers. There are two types of routing protocols which are used in inter-networks: interior gateway protocols (IGPs) and exterior gateway protocols (EGPs).
IGP is used to exchange routing information with routers in the same autonomous system (AS). An AS is a collection of networks under common administrative domain. In a AS all the routers basically share the same routing information. Eg. EIGRP, RIP, etc.
EGP is used to communicate between different ASes. Eg. BGP (Border Gateway Protocol)
Administrative distance (AD) defines the trustworthiness of the routing information received on a router from a neighbor router. It is an integer ranges from 0 to 255. O is the most trusted and 255 is the least trusted or no traffic will pass through it.
Default administrative distances:
* We can manually define the AD for static route also:
rtr# ip route <destinationNetwork> <subnetMask> <gatewayIP> <AD>
Routing Protocols
Routing protocols are categorized into three classes according to their working function:
Distance Vector: The best path to the destination network is calculated and judged by distance. Eg. if a packet is passed through a router it is count a hop. The route with the least number of hops to the network is determined to be the best route to the destination. E.g. RIP and IGRP.
Link State: These routing protocols send updates containing the state of their own links to the other directly connected routers on the network, which is then propagated to their neighbors. They keeps track of directly attached neighbors, topology of the entire inter-network and the routing table. Eg. OSPF and IS-IS.
Hybrid: They are the protocols with both the characters of distance vector and link state. It sends traditional distance-vector updates containing information about networks plus the cost of reaching them from the perspective of the advertising router. E.g. EIGRP. It is the propitiatory of CISCO.
IGP is used to exchange routing information with routers in the same autonomous system (AS). An AS is a collection of networks under common administrative domain. In a AS all the routers basically share the same routing information. Eg. EIGRP, RIP, etc.
EGP is used to communicate between different ASes. Eg. BGP (Border Gateway Protocol)
Administrative distance (AD) defines the trustworthiness of the routing information received on a router from a neighbor router. It is an integer ranges from 0 to 255. O is the most trusted and 255 is the least trusted or no traffic will pass through it.
Default administrative distances:
* We can manually define the AD for static route also:
rtr# ip route <destinationNetwork> <subnetMask> <gatewayIP> <AD>
Routing Protocols
Routing protocols are categorized into three classes according to their working function:
Distance Vector: The best path to the destination network is calculated and judged by distance. Eg. if a packet is passed through a router it is count a hop. The route with the least number of hops to the network is determined to be the best route to the destination. E.g. RIP and IGRP.
Link State: These routing protocols send updates containing the state of their own links to the other directly connected routers on the network, which is then propagated to their neighbors. They keeps track of directly attached neighbors, topology of the entire inter-network and the routing table. Eg. OSPF and IS-IS.
Hybrid: They are the protocols with both the characters of distance vector and link state. It sends traditional distance-vector updates containing information about networks plus the cost of reaching them from the perspective of the advertising router. E.g. EIGRP. It is the propitiatory of CISCO.